Defense
Brief About How Defense System Works
A defense system works by integrating multiple components to detect, intercept, and neutralize potential threats. Here’s a brief overview:
- Detection: Utilizes radar and satellite technology to identify incoming threats, such as missiles or aircraft.
- Interception: Employs various weapons, including missiles and anti-aircraft guns, to engage and destroy the identified threats.
- Command and Control: Involves a network of command centers that process information, coordinate defense assets, and issue orders.
- Communication: Relies on secure communication channels to relay information and instructions between different parts of the defense system.
GIS BASED INTELLIGENCE ANALYSIS SYSTEM
A GIS-based Intelligence Analysis System integrates geographic information system (GIS) technology with intelligence data to enhance spatial analysis and decision-making. It enables the visualization, analysis, and interpretation of complex data sets through maps and geospatial data. This system supports tasks such as threat assessment, route planning, and resource allocation by providing a comprehensive spatial context.
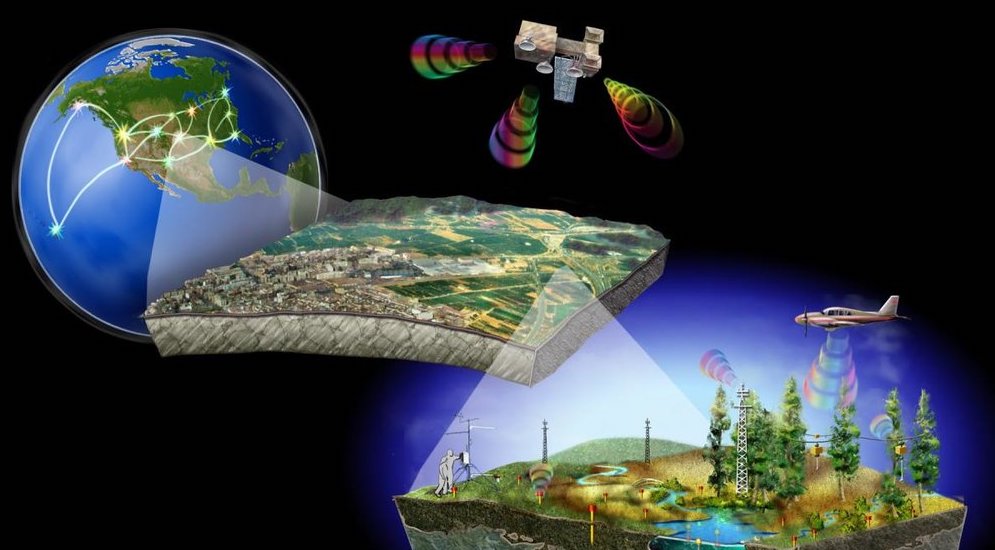
The system offers real-time data on probabilities, hostile territories, insurgent and terrorist movements, and prevalent weapon types within designated areas.
The system offers real-time data on probabilities, hostile territories, insurgent and terrorist movements, and prevalent weapon types within designated areas.
Facilitating rapid deployment, commanders gain insights into the time needed for asset and manpower mobilization, streamlining operational efficiency.
By streamlining operations, the system effectively curtails base operation and maintenance expenses.
FLEET TRACKING SYSTEM
A Fleet Tracking System is a technology-based solution that utilizes GPS and data analytics to monitor and manage vehicle fleets. It provides real-time location tracking, driver behavior analysis, and vehicle diagnostics to improve efficiency and safety. These systems help businesses optimize routes, reduce fuel consumption, ensure timely maintenance, and enhance regulatory compliance. By leveraging telematics, fleet tracking systems offer valuable insights into fleet operations, leading to cost savings and improved service delivery.
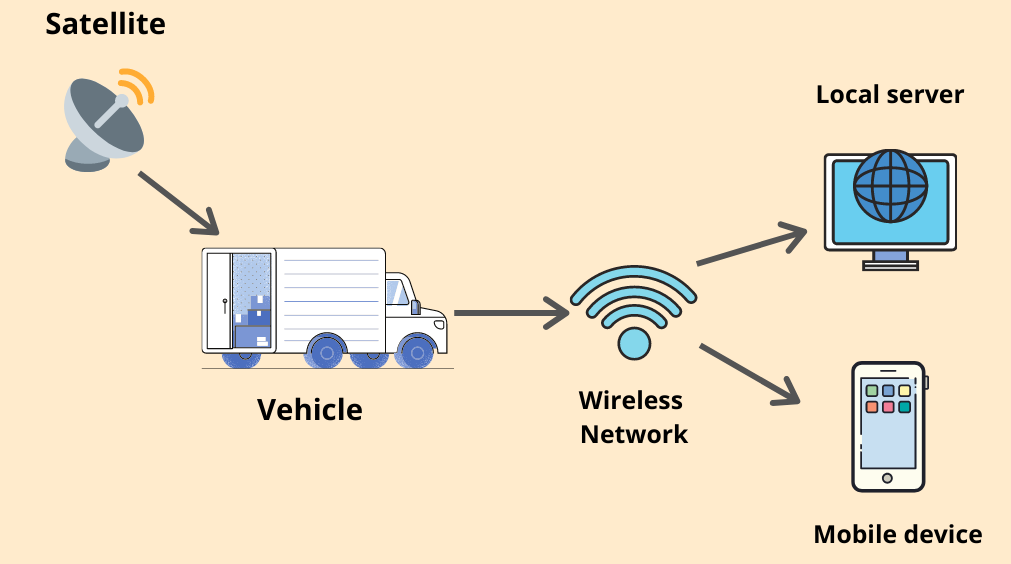
Fleet tracking systems provide precise, real-time location data for each vehicle. This enables better route management, immediate response to emergencies.
Monitoring driver behavior leads to improved performance. It identifies areas for training, promotes safe driving practices, and reduces unauthorized vehicle use.
These systems optimize fuel usage and maintenance schedules, leading to significant cost savings. By minimizing idle times and improving route planning.
Fleet tracking offers comprehensive reporting features, delivering insights into fleet utilization and efficiency. Data-driven decisions can be made to streamline operations
CYBER SECURITY TOOLS
Cybersecurity tools are essential for defending against digital threats. They include antivirus software, firewalls, intrusion detection systems (IDS), and virtual private networks (VPN). These tools protect against malware, unauthorized access, and data breaches. Antivirus programs detect and remove malicious software; firewalls control incoming and outgoing network traffic; IDS monitor for suspicious activities; and VPNs encrypt internet connections. Together, they form a multi-layered defense, safeguarding information and systems in an increasingly connected world

Antivirus software is the first line of defense in cybersecurity. It scans computers and networks for malicious code and activity, identifying and removing viruses, worms, and trojans.
Firewalls act as a barrier between trusted and untrusted networks, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules.
IDPS tools are critical for identifying potential threats and responding to them in real-time. They analyze network traffic to detect patterns indicative of cyber attacks, such as unusual data transfers or protocol activities
VPNs create a secure, encrypted connection over a less secure network, like the internet. They ensure that sensitive data transmitted between remote users and the company network remains confidential and protected from eavesdropping.
CENTRAILSED E-CARD SYSTEM
A centralized e-card system integrates various card-based services into a unified digital platform. It simplifies the management and use of e-cards for transactions, identification, and access across multiple sectors. This system enhances security, reduces administrative costs, and provides user convenience. It’s particularly useful in banking, corporate access, and public services, enabling efficient and secure electronic interactions. Centralized e-card systems ensure consistent standards.
Centralized e-card systems offer robust security features, safeguarding personal and financial data against unauthorized access and fraud.
By streamlining card management processes, centralized e-card systems significantly improve operational efficiency.
Centralized e-card systems provide unparalleled convenience by allowing users to access multiple services with a single card.
These systems collect vast amounts of data, which can be analyzed to gain insights into consumer behavior, spending patterns, and service usage.
CAMPUS SECURITY SOLUTIONS WITH VIDEO ANALYTICS
Campus security solutions with video analytics use AI to monitor and analyze video feeds in real-time, enhancing safety and efficiency. They detect unusual activities, manage crowd control, and identify potential threats, providing immediate alerts. This proactive surveillance assists in preventing incidents and facilitates quick response to emergencies.

Campus security solutions with video analytics proactively detect potential threats through continuous monitoring.
These systems manage a vast network of cameras, applying advanced analytics for tasks like facial recognition and object tracking.
Video analytics facilitate instant alerts, allowing security personnel to respond quickly to incidents.
The integration of video analytics yields valuable data, offering insights into campus activity patterns.
PRISON CALLING SYSTEM
A Prison Calling System (PCS) is a controlled telecommunication service that allows inmates to maintain contact with the outside world. PCS typically operates via secure kiosks or phones within the facility, with calls being monitored for security purposes. Inmates have access to pre-approved numbers and are allotted a specific call duration to ensure fair usage. This system is crucial for supporting rehabilitation by preserving family ties and aiding in legal proceedings

To initiate calls, inmates within the prison facility are required to enroll in the system using a fingerprint scanner, along with providing personal details such as name, date of birth, and address.
Prior to placing calls, inmates undergo authentication by providing their fingerprints, thus mitigating the risk of unauthorized activities within the prison premises.
Once registered in the system, inmates gain access to make calls via designated kiosks, allowing them to dial recipient numbers and initiate communication.
Administrators have the capability to impose call duration limits for inmates based on predefined criteria, ensuring adherence to regulations and operational guidelines.
SOLDIER TRACKING SYSTEM
A Soldier Tracking System (STS) is a technological framework designed to monitor and ensure the safety of soldiers during operations. Utilizing IoT, GPS, and biometric sensors, STS provides real-time data on soldiers’ locations, health status, and environmental conditions. It enables command centers to track movements, monitor vital signs like heart rate and temperature, and respond swiftly to emergencies.
(STS) provide real-time location data using GPS, enabling command centers to monitor troop movements and coordinate operations effectively
STS incorporates biometric sensors to track soldiers’ vital signs, such as heart rate and body temperature, allowing for immediate medical intervention
By integrating environmental sensors, STS can alert soldiers to potential hazards like gas leaks or extreme temperature changes,
STS facilitates seamless communication between soldiers and command units, ensuring efficient mission executions
ARMS & AMMUNITION MANAGEMENT SYSTEM
An Arms & Ammunition Management System (AAMS) is a comprehensive framework designed to regulate and track the lifecycle of firearms and munitions. It ensures secure storage, controlled distribution, and accountability of arms and ammunition within military, law enforcement, and licensed civilian entities. AAMS incorporates inventory management, usage logging, and maintenance schedules, often using barcoding or RFID technology for efficient tracking.

An Arms & Ammunition Management System (AAMS) meticulously tracks inventory, ensuring that each item is accounted for from acquisition to disposal.
AAMS ensures adherence to strict regulations governing arms and ammunition, documenting every transaction and maintaining detailed records for legal and safety requirements
The system schedules regular maintenance and inspections, guaranteeing that all arms and ammunition are in optimal condition and ready for use when needed
AAMS monitors the distribution and usage of arms, providing insights into patterns that can inform future procurement and allocation decisions
